Getty Images
Researchers have discovered previously unknown Mac malware infecting a cryptocurrency exchange. It contains a full suite of capabilities, including the ability to steal private data and download and execute new malicious files.
Dubbed JokerSpy, the malware is written in the Python programming language and makes use of an open source tool known as SwiftBelt, which is designed for legitimate security professionals to test their networks for vulnerabilities. JokerSpy first came to light earlier this month in this post from the security firm Bitdefender. Researchers for the company said they identified Windows and Linux components, suggesting that versions exist for those platforms as well.
Five days later, researchers for security firm Elastic reported that the diagnostic endpoint protection tool they sell had detected xcc, a binary file that’s part of JokerSpy. Elastic didn’t identify the victim other than to say it was a “prominent Japanese cryptocurrency exchange.”
Once xcc executed, the unknown threat actor attempted to bypass so-called TCC protections in macOS that require explicit permission from a user before an app can access a Mac’s hard drive, contacts, and other sensitive resources or record its screen.
By replacing the existing TCC database with their own, the threat actors were likely trying to suppress alerts that would otherwise appear when JokerSpy runs. In past attacks, threat actors have been able to bypass TCC protections by exploiting vulnerabilities in them. Researchers have also demonstrated attacks that were able to do the same thing.
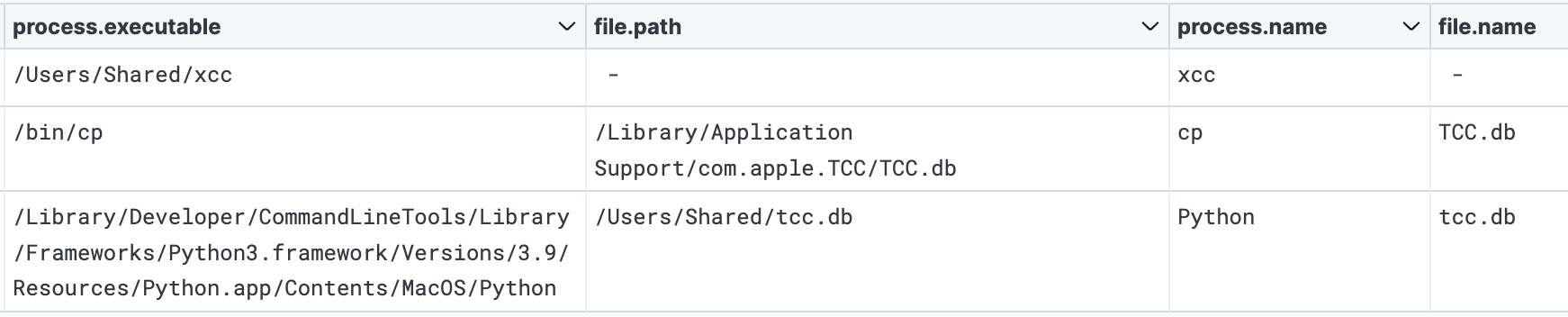
Threat actor creating/modifying and moving a TCC database, and then executing xcc.
Elastic
The xcc executable checks the TCC permissions and identifies the app the user is currently interacting with. It then downloads and installs sh.py, the main engine for the JokerSpy malware. It contains the usual backdoor capabilities, including:
| Command | Description |
|---|---|
| sk | Stop the backdoor’s execution |
| l | List the files of the path provided as parameter |
| c | Execute and return the output of a shell command |
| cd | Change directory and return the new path |
| xs | Execute a Python code given as a parameter in the current context |
| xsi | Decode a Base64-encoded Python code given as a parameter, compile it, then execute it |
| r | Remove a file or directory from the system |
| e | Execute a file from the system with or without parameter |
| u | Upload a file to the infected system |
| d | Download a file from the infected system |
| g | Get the current malware’s configuration stored in the configuration file |
| w | Override the malware’s configuration file with new values |
“Once a system is compromised and infected with malware like JokerSpy, the attacker effectively has a great degree of control over the system,” researchers with macOS security firm Intego wrote on Friday. “With a backdoor, attackers can install additional components in the background and could potentially run further exploits, monitor users’ behavior, steal login credentials or cryptocurrency wallets, and more.”
Researchers still aren’t sure how JokerSpy gets installed. Elastic researchers said they “strongly believe that the initial access for this malware was a malicious or backdoored plugin or 3rd party dependency that provided the threat actor access.” This theory aligns with observations from researchers at Bitdefender who correlated a hardcoded domain found in a version of the sh.py backdoor to a series of tweets about an infected macOS QR code reader that was found to have a malicious dependency. Elastic also said the threat actor it observed already had “existing access” to the Japanese cryptocurrency exchange.
The posts linked above list various indicators that people can use to determine if they’ve been targeted with JokerSpy. Besides cryptographic hashes of various samples of xcc and sh.py, indicators include contact with domains at git-hub[.]me and app.influmarket[.]org. While JokerSpy went undetected by the vast majority of antivirus engines when the malware first came to light, a much wider body of engines is able to identify it now. While there is no confirmation that Windows or Linux versions of JokerSpy exist, people should be aware that’s a distinct possibility.







